
Introduction
In the digital age, understanding how web applications authenticate users is crucial. Two key concepts in this realm are cookies and sessions. While they may seem similar at first glance, they serve distinct purposes in the process of user authentication. This article breaks down these concepts using a practical example: logging into your bank account.
The Login Process
Imagine you want to log in to your bank account. You’re presented with a login screen where you enter your username and password. After clicking the login button, your credentials are sent to the bank’s server. Nowadays, this login process often includes an additional verification step, such as receiving a text message, but we’ll simplify it for clarity.
How the Server Verifies Your Identity
Once your information reaches the server, it must verify your identity. The bank’s server checks its database to confirm that your credentials are correct. If everything checks out, you’ll be directed to your account overview page. However, there’s more happening behind the scenes.
Creating a Session ID
After validating your credentials, the server records your login event in the database and assigns you a session ID, which is stored in the form of a cookie. In essence, you’ve exchanged your username and password for a cookie that contains this session ID. Think of the session ID as a unique identifier for your login session, randomly generated for security. It’s akin to receiving a coat check ticket at a restaurant.
Observing the Login Process
Imagine you want to log in to your bank account. You’re presented with a login screen where you enter your username and password. After clicking the login button, your credentials are sent to the bank’s server. Nowadays, this login process often includes an additional verification step, such as receiving a text message, but we’ll simplify it for clarity.
How the Server Verifies Your Identity
Once your information reaches the server, it must verify your identity. The bank’s server checks its database to confirm that your credentials are correct. If everything checks out, you’ll be directed to your account overview page. However, there’s more happening behind the scenes.
Creating a Session ID
After validating your credentials, the server records your login event in the database and assigns you a session ID, which is stored in the form of a cookie. In essence, you’ve exchanged your username and password for a cookie that contains this session ID. Think of the session ID as a unique identifier for your login session, randomly generated for security. It’s akin to receiving a coat check ticket at a restaurant.
Observing the Login Process
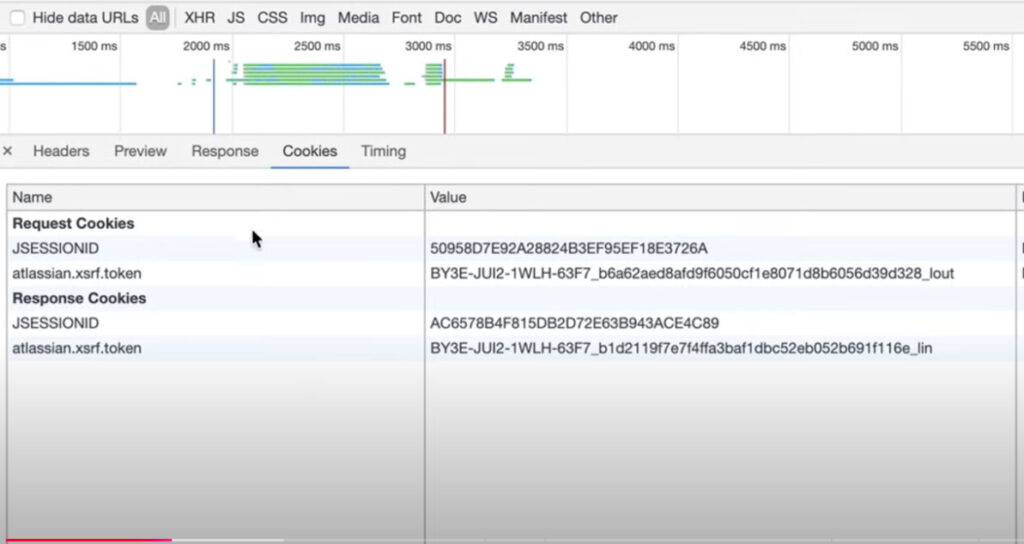
For a deeper dive into cookies, I’ve written another tutorial, which you can find linked in the description. You can observe this login process on nearly any website. In browsers like Google Chrome, you can open the developer tools to inspect your network traffic. For example, after entering my username and password, I received a cookie with my session ID.
The Role of Cookies
The contents of this cookie remain confidential and cannot be accessed by other websites. The server stores the session information in its database, while only the session ID is kept in a cookie on your computer. The next time you request another page, your browser automatically sends the cookie with your session ID. The server checks this ID to verify its validity./
Importance of Security
It’s important to note that during subsequent requests, you won’t need to re-enter your username and password to identify yourself. However, if you log out, your login session is invalidated in the database, and the server instructs your browser to delete the cookie containing the session ID. If the server session expires due to inactivity, the cookie becomes useless. For example, if you remain inactive for a specified time, such as five minutes, your bank may require you to log in again.
An Analogy for Cookies
To illustrate the cookie concept, think of it as your gym membership card. The card holds your member ID, and when you scan it at the gym’s entrance, it verifies that your membership is still valid, granting you access. Similar to your gym card, a session ID cookie only works for a specific website; you can’t use it to enter your office building, for instance. If your gym membership expires, your card will no longer be valid.
Cookie-Based Authentication
Returning to our login example, this method is known as cookie-based authentication. The server handles the session, while the cookie serves as a convenient way to transport the session ID. Browsers automatically send cookies with every request. Cookies are transmitted using HTTP headers in the messages exchanged between the browser (the client) and the server. HTTP is the protocol that enables communication between them.
Why Use a Server-Side Session?
In this case, the bank stores the session information on the server side, meaning you can’t see its contents, which also prevents you from manipulating any data. One reason servers refrain from storing excessive information in cookies is due to security concerns, as cookies originate from the client. Relying on client-side data is like telling the bank you have a million dollars in your account and expecting them to take your word for it. This is why servers prefer to work with their databases, where only validated information exists.
Summary of Key Points
To summarize: the session is generated by the server and stored in a database, while the client receives only the session ID. This session ID is a meaningless, randomly generated sequence that’s hard to guess.
Token-Based Authentication: A Modern Alternative
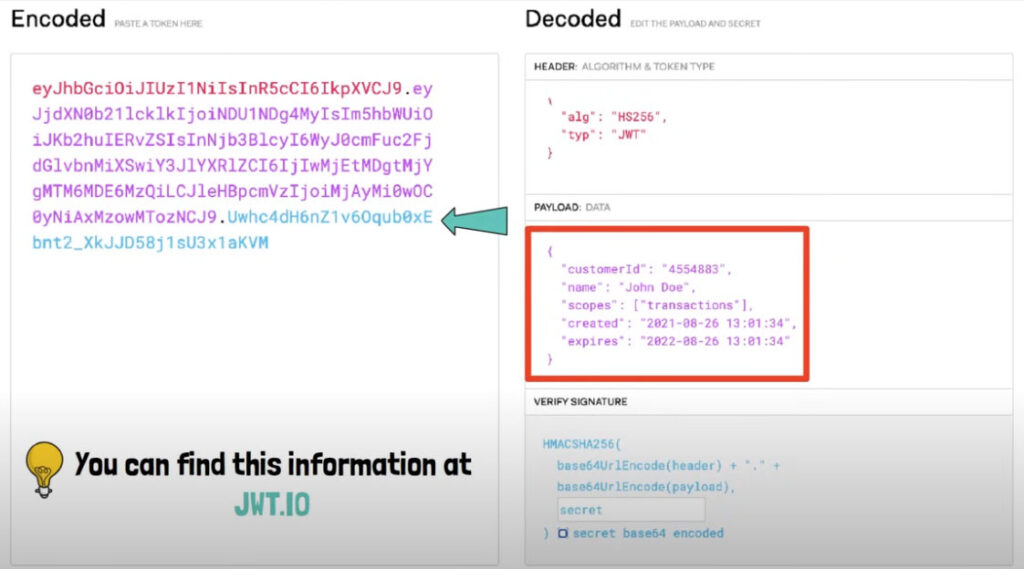
Traditional cookie-based authentication has worked well for many years, but it is becoming outdated for certain applications. Consider the scenario of installing a financial app on your phone. You wouldn’t want to provide your username and password to an app that isn’t verified by your bank. Instead, the app would redirect you to your bank’s login page, where you would enter your credentials. After authentication, the bank would ask if you’d like to grant the app access to your transactions. If you consent, the app receives a token allowing limited access to your data.
Conclusion
In this exchange, you never expose your username and password beyond the initial authentication with the bank. If needed, you can easily revoke access to your account by invalidating the token, which is separate from your password. While cookies and sessions are essential for authentication, tokens offer a modern and secure alternative for granting access to third-party applications. Understanding both systems is vital for navigating the complexities of user authentication in today’s digital landscape.

